One of the most extensive functionalities within our plugin is the login firewall. It encompasses several tables displaying statuses, and various actions can also be executed. This article will provide a thorough guide to help you effectively manage these events.
Active Lockouts
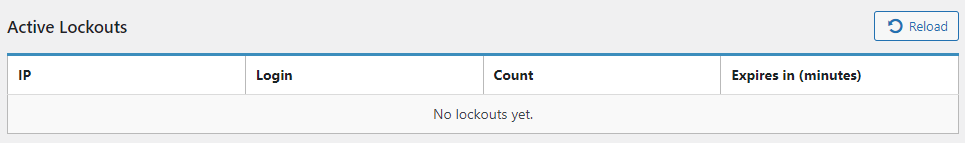
This section provides a list of all lockouts that are currently active and enabled. When an active lockout is present, It contains the IP address, the Login name, how many attempts were made (Count), and when the lockout will expire (Expires in minutes).
Event Log
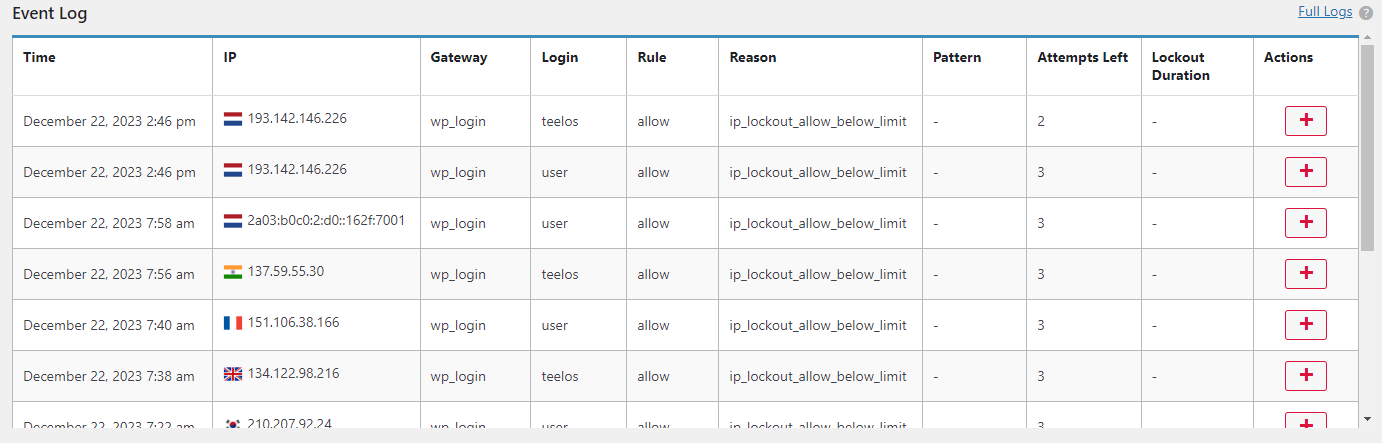
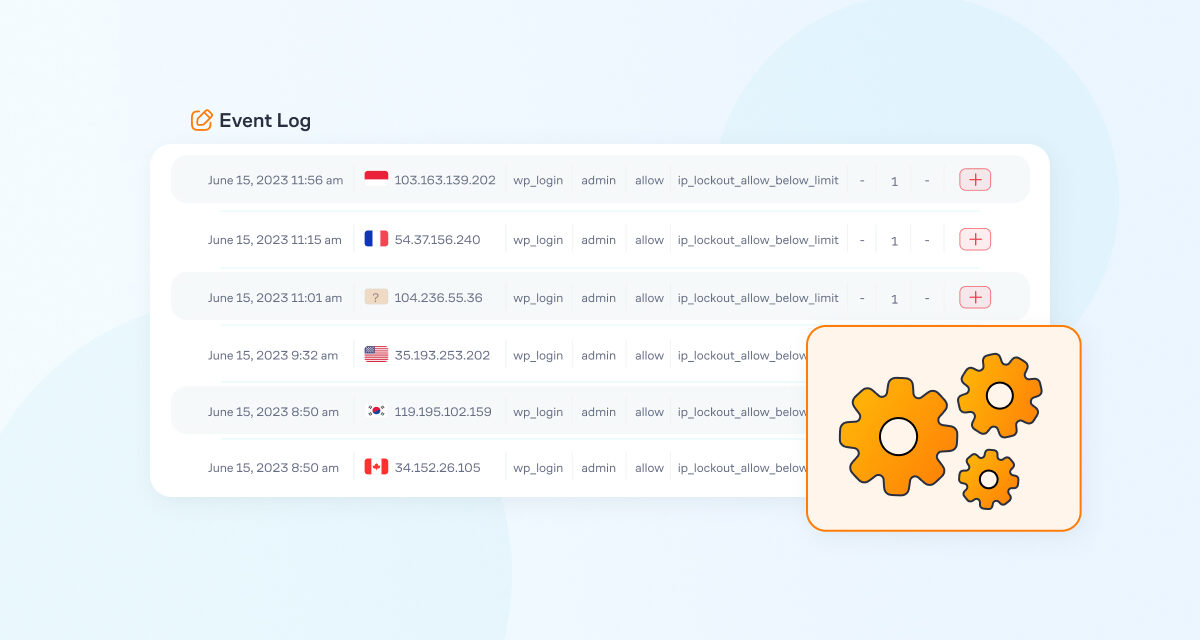
This is a log of all login attempts for your website.
Definitions
Time: the time the attempt was recorded (using the time configured on your site).
IP: IP address associated with the attempt.
Gateway: The URL that was used by the attack.
Login: Username that was used in the attack.
Rule: The rule that was triggered. It's either allow or deny.
Reason: There are quite a few different statuses available here:
- ip_acl_temp_local_deny - IP blocked temporary for this site only
- ip_acl_temp_network_deny - IP blocked temporary for the group of sites this site belongs to
- ip_acl_local_deny - IP blocked by allow/deny rules for this site only
- ip_acl_network_deny - IP blocked by allow/deny rules for the group of sites this site belongs to
- ip_lockout_allow_expired - IP allowed b/c its lockout period has expired
- ip_lockout_allow_below_limit - IP allowed b/c the number of attempts is below limit
- ip_lockout_deny - IP is locked out b/c the number of attempts is above limit
- ip_acl_xmlrpc_deny - IP is locked out b/c the XML-RPC gateway is closed
- login_acl_local_pass - attempt allowed b/c of a local login pass rule
- ip_acl_local_pass - attempt allowed b/c of a local ip pass rule
- all_acl_none - there were no allow/deny rules matching the request
- country_acl_local_allow - the country is allowed for this site
- country_acl_local_deny - the country is denied for this site
- ip_acl_temp_none - IP is not blocked temporary
- all_acl_local_allow - both IP and login are allowed by allow rules for this site only
- all_acl_network_allow - both IP and login are allowed by allow/deny rules for the group of sites this site belongs too
- login_acl_network_deny - login is blocked by a deny rule for the group of sites this site belongs too
- login_acl_local_deny - login is blocked by a deny rule for this site onl
Pattern: A username that you listed, an IP or range of IPs, a country. This is an entity based on which the decision was made to allow or deny an attempt.
Attempts Left: How many attempts are left for the IP at the time the attempt happened.
Lockout Duration: How many minutes are left before the IP is unlocked automatically, at the time the attempt happened.
Actions: You can add or remove IPs and logins to/from your allow/deny lists.
Icon Definitions for Actions:
| Open Red lock | Unlock IP (release an active automatic lockout). This will enable the user with that IP address to continue login attempts according to the Allowed Retries setting value (normally 3 or 4). | |
| Red Plus sign | Add IP or login to deny rules. Add IP or login to deny rules. This will completely prevent the user from logging in successfully as long as no other conflicting pass rules were created. | |
| Red Minus sign | Remove IP or login from deny rules. This will allow the user to log in again. | |
| Green Plus sign | Add IP or login to allow rules. This will white-list the user to be able to log in without any restrictions. |
Login Access Rules
To improve your protection against brute force attacks you can specify Login and IP-based access rules. You can add these rules in two places: In the Login Firewall of the LLAR plugin, and/or in your billing account. This feature is not available for free users.