To improve your protection against brute force attacks you can specify Login and IP-based access rules. You can add these rules in two places: In the Login Firewall of the LLAR plugin, and/or in your billing account. This feature is not available for free users.
When rules are added directly to the plugin, they will exclusively apply to your website. If performed within your LLAR billing account, the rules will have a universal effect on all websites associated with your account. If implemented in both locations, the rules will synergize; however, the local rules will hold precedence over the global rules, with the exception of the Pass rule (refer to details below).
Rule Types
There are currently 3 types of rules:
Deny
All attempts matching this rule will always be denied unless there is an allow rule that overrides it.
Allow
All attempts matching this rule will be allowed to try to log in. This is the default behavior for any attempt - users can try to log in, but the attempt will be checked using our cloud's security intelligence algorithms (in addition to your own access rules). Use the allow rule when you need to make an exclusion from the deny rule (see examples below).
Pass
All attempts matching this rule will go through without any verification and penalty. This is the default behavior as though the LLAR plugin is not installed, so use this at your own risk! We don't recommend using this rule. Also, note that the pass rule is the most powerful rule and it overrides any other rule. For example, if you denied an IP locally within the site's settings, but added the same IP in your LLAR account with the pass rule, the pass rule will still take priority.
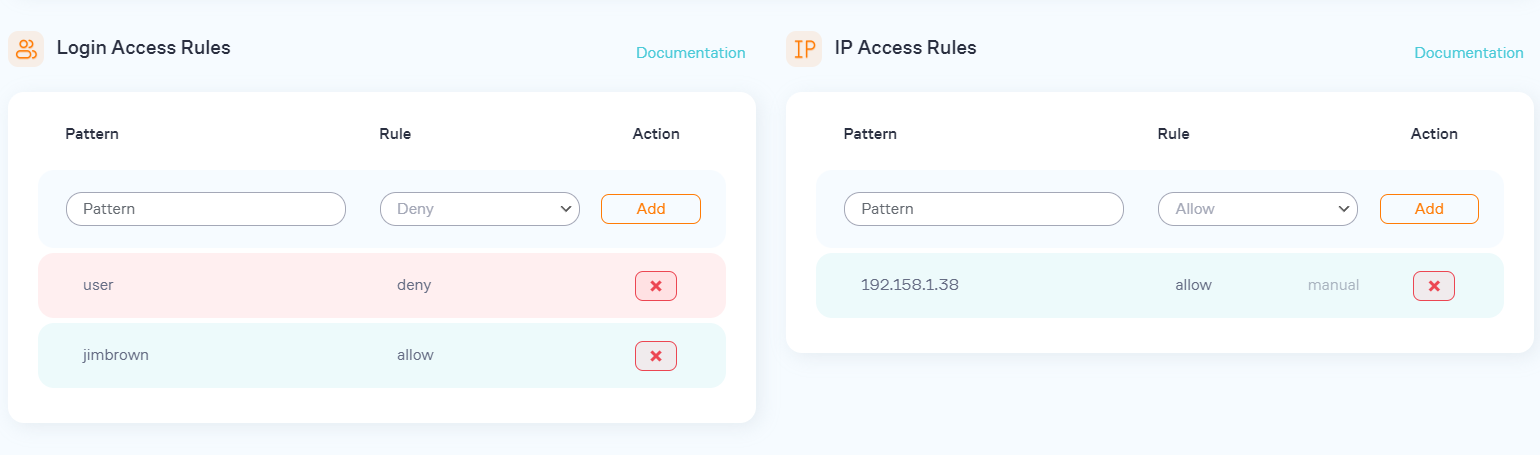
Login Access Rules Examples
| Pattern: admin Rule: deny Result: All attempts from the "admin" username will be denied. |
You can use "*" and "?" in your login (not IP) patterns. "*" replaces any number of characters, "?" replaces just one character.
| Pattern 1: * Rule 1: deny Pattern 2: admin Rule 2: allow Result: Attempts from any username other than "admin" will be denied. |
| Pattern: admin Rule: pass Result: All attempts from the "admin" username will be allowed w/o any limit. Don't do that unless you 100% sure that's what you want. |
IP Access Rules Examples
| Pattern: 10.0.0.0 Rule: deny Result: All attempts from the 10.0.0.0 IP will be denied. |
You can use CIDR notation.
| Pattern: 10.0.0.0/24 Rule: deny Result: All attempts from the 10.0.0.0-10.0.0.255 IP range will be denied. |
Human-friendly ranges are supported too.
| Pattern: 10.0.0.0-10.0.0.255 Rule: deny Result: All attempts from the 10.0.0.0-10.0.0.255 IP range will be denied. |
| Pattern 1: 10.0.0.0/24 Rule 1: deny Pattern 2: 10.0.0.10 Rule 2: allow Result: All attempts from the 10.0.0.0-10.0.0.255 IP range excluding 10.0.0.10 will be denied. |
IPv6 are supported too - using both individual and CIDR notations.
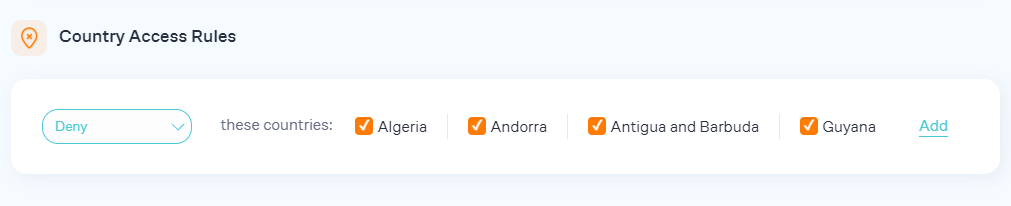
Block Logins By Country
Within the Login Firewall, you can choose to restrict logins based on the country. Alongside establishing access rules, we strongly advise setting up this feature to significantly minimize your vulnerability to brute force attacks. You can opt to permit only specific countries or designate certain countries to be denied access.