Brute force attacks are relentless and automated attempts to crack passwords or encryption keys by systematically trying all possible combinations until the correct one is found. They target vulnerabilities in websites, making them a major concern for individuals and organizations alike. Cybercriminals frequently target WordPress websites, making the implementation of login security protocols and brute force protection tools the most effective defense. Let's explore their functionality and discuss measures you can take to safeguard your WordPress websites.
Why Are Brute Force Attacks So Common in WordPress?
WordPress is used by over 40% of the internet, making it a prime target for cybercriminals. Brute force attacks are commonly targeted at WordPress due to factors such as default login credentials, weak passwords, outdated software, and the prevalence of publicly accessible login pages. They use automated scripts to scan the internet randomly for victims, even though the success rate is low. It's a numbers game for them, hoping for results eventually.
How Do Brute Force Attacks Work?
Brute force attacks typically involve a systematic process where hackers employ automated tools to exhaustively try all possible combinations of passwords or encryption keys until the correct one is discovered. The process can be broken down into steps:
Step #1 - Target Selection
- The attacker identifies a target, such as a user account, network, or system, that they want to compromise. Most attacks in WordPress are done at random. Websites are typically discovered from shared servers and domain databases.
Step # 2 - Enumeration
- Before launching the brute force attack, the hacker performs enumeration to gather information about the target, such as valid usernames, email addresses, or system details.
Step #3 - Password Guessing
- The attacker employs specialized software or scripts to systematically guess passwords. There are different methods at guessing a password. The most popular method is a dictionary attack, which involves using precompiled dictionaries of commonly used passwords. These dictionaries may include words from various languages, character substitutions, and common phrases. This can involve trying every conceivable combination, starting from the simplest and most common passwords to more complex ones.
Step #4 - Continuous Iteration
- The attack continues until the correct password or key is discovered, potentially granting the attacker unauthorized access to the target system.

When Do Attacks Typically Occur?
Brute force attacks in WordPress can occur at any time throughout the year, and their prevalence is not necessarily tied to a specific season or time frame. Nevertheless, Limit Login Attempts Reloaded suggests that instances of brute force attacks might increase during periods of heightened internet traffic, such as holiday shopping seasons or significant global events like the Olympics. Websites tend to be at their highest vulnerability when the potential impact of a successful attack is most significant, often occurring during periods of heightened traffic or increased sales.
The Vulnerability Equation
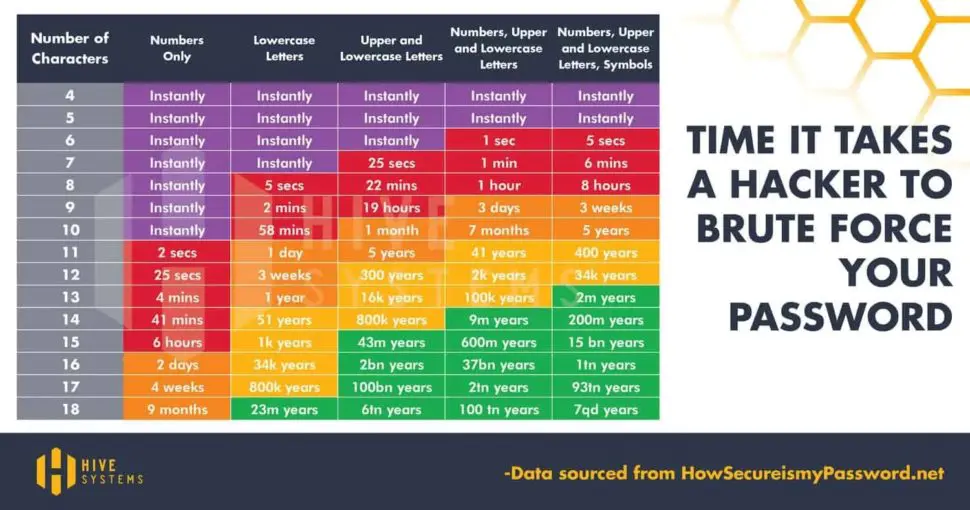
Brute force attacks are particularly effective against weak passwords. A strong, complex password acts as a formidable barrier against such attacks. It should include a combination of uppercase and lowercase letters, numbers, and special characters. Remember, the longer and more unique your password, the harder it is for attackers to crack. According to Komando, If your password comprises numbers, upper and lowercase letters and symbols, it will take a hacker 34,000 years to crack – if it’s 12 characters long.
What Is WordPress Doing About Brute Force Attacks?
WordPress places a significant emphasis on security measures to address the persistent threat of brute force attacks. To enhance protection for its users, WordPress has implemented several proactive measures.
One notable strategy involves the integration of strong password policies and the encouragement of complex, unique passwords. Additionally, the platform supports the use of multi-factor authentication (MFA), adding an extra layer of defense against unauthorized access attempts. Furthermore, WordPress regularly releases security updates to address potential vulnerabilities, ensuring that users benefit from the latest security enhancements.
Moreover, the WordPress community has released several tools and plugins to protect website from brute force attacks. One notable plugin is Limit Login Attempts Reloaded, which limits the amount of login attempts an IP address can make. The plugin is free to use, and boasts over 2 million active installs.

How Can I Protect My WordPress Website From Brute Force Attacks?
Ensuring advanced protection against brute force attacks in WordPress doesn't require complex solutions: Utilize robust passwords, restrict login attempts, regularly update plugins, and conduct audits of user accounts. More advanced measures include 2FA, deny logins by country, and intelligent IP detection. The effectiveness of brute force attacks significantly diminishes when administrators prioritize security measures.
Knowledge is Power
Now that you understand the mechanics behind brute force attacks, you possess a powerful weapon in the ongoing battle against cyber threats. By staying informed and employing robust security practices, you can significantly reduce the risk of falling victim to such attacks.
Remember, vigilance and proactive measures are key to maintaining a secure digital presence. Stay tuned for future blogs as we continue to explore various cybersecurity topics and empower you with the knowledge you need to protect yourself in the ever-evolving digital landscape.
Frequently Asked Questions
A brute force attack is a malicious attempt to gain unauthorized access by systematically trying all possible combinations of passwords or keys. In the context of WordPress, attackers target the login page, attempting various username and password combinations until they find the correct one.
Common signs of a brute force attack include a sudden spike in failed login attempts, increased server load, and unusual activity in server logs.
Yes, recommended security measures include using strong, unique passwords, limiting login attempts, keeping WordPress core, themes, and plugins updated.
The best plugin for preventing brute force attacks is Limit Login Attempts Reloaded. The plugin boasts over 2 million active installs and a 4.9/5 rating on WordPress.org.