Securing the login process for WordPress administrators is paramount in safeguarding sensitive data and ensuring the overall integrity of a website. In this article, we'll outline a comprehensive checklist of essential login security policies that organizations should implement for their WordPress administrators. Following these guidelines will significantly reduce the risk of unauthorized access, data breaches, and other security threats.
Importance of Implementing Guidelines In Your Organization
Creating login security guidelines in an organization is crucial for several reasons, all of which contribute to safeguarding sensitive information, maintaining the integrity of systems, and mitigating the risks associated with unauthorized access. According to IBM's annual "Cost of a Data Breach" report, the global average cost of a data breach in 2023 was $4.45 million. This figure considers various expenses, including detection and escalation, notification, response, and lost business.

5 key reasons why implementing login security protocols is important
Let's review why your organization should be implementing login security controls.
#1 - Protection Against Unauthorized Access
Login security guidelines help protect organizational assets, data, and systems from unauthorized access. By implementing strong authentication measures, such as complex passwords and two-factor authentication (2FA), organizations can significantly reduce the risk of unauthorized entry.
#2 - Prevention of Data Breaches
Strong login security measures are a frontline defense against data breaches. Unauthorized access to sensitive information can lead to data leaks, financial losses, and damage to an organization's reputation. Login security guidelines help prevent such breaches by setting standards for access control and authentication.
#3 - Protection of User Identities
Login security guidelines are essential for protecting the identities of users, employees, and administrators. Compromised login credentials can lead to identity theft and unauthorized use of personal information. Robust security measures help maintain the confidentiality of user identities.
Success Stories Hundreds of Agencies Across The World Use LLAR





#4 - Protection of Financial Assets
Financial transactions and sensitive financial information are often managed through online systems. Strong login security guidelines protect these assets by ensuring that only authorized personnel have access to financial data and transactions.
#5 - Mitigation of Insider Threats
Insider threats, whether intentional or unintentional, pose a significant risk to organizations. Login security guidelines help mitigate these threats by implementing access controls, monitoring user activity, and ensuring that employees have only the necessary permissions for their roles.
How To Implement A Login Security Program [Step-by-Step Guide]
You don't need to be a WordPress expert to implement robust login security policies. Follow these simple steps and secure the future of your organization.
Step #1 - Designate a member of your organization
Before implementation, designate a responsible individual or team within your organization to manage the program. This person or group should possess administrative permissions for your website and a thorough understanding of its functionalities. In many cases, this responsibility may fall on the company owner. Their role involves regularly reviewing the program, verifying that all website users are identified, and confirming adherence to the established guidelines.
Step #2 - Implement the login security checklist
Ensure your assigned individual thoroughly reviews the checklist to comprehend each requirement. Initiate the implementation of each item and continue until all tasks are finalized. Upon completion, store the finalized checklist, and ensure the assigned individual provides their signature before filing the document. This practice may prove beneficial in the event of a data breach, serving as documentation in case questions arise concerning your security protocols.
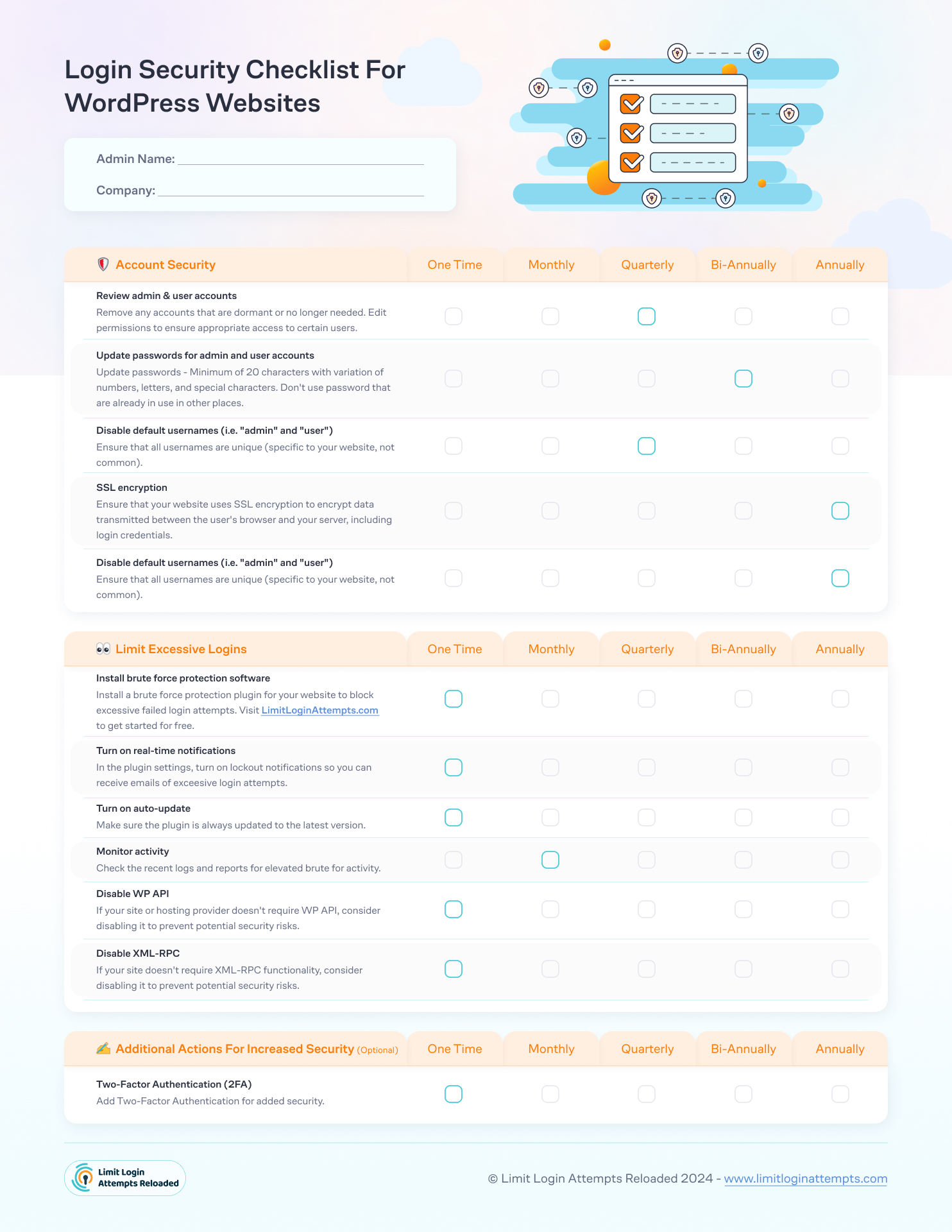
Step #3 - Review monthly, quarterly, and yearly
Certain checklist items may require monthly, quarterly, or annual actions, so make sure to plan accordingly for the review of these guidelines. We highly recommend using the IP logs from the Limit Login Attempts Reloaded dashboard to review activity on your website.
Conclusion
In conclusion, safeguarding your organization's WordPress login security is paramount in today's digital landscape. By implementing the comprehensive checklist provided in this article, you empower your team to fortify the first line of defense against potential threats. Strengthening password policies, enabling two-factor authentication, and regularly monitoring user access are crucial steps toward maintaining a secure WordPress environment. Remember, a well-secured WordPress login is not just a safeguard; it's a commitment to the integrity and resilience of your organization's online presence.
Frequently Asked Questions
We recommend at the least every 6 months, but the more the better.
Strong passwords, disabling common usernames, SSL encryption, and reviewing user permissions are can greatly improve your login security.
The best brute force protection software is Limit Login Attempts Reloaded, which has over 2 million active installs.
We recommend reviewing your policies at least once a year due to evolving threats.