Premium subscribers will notice that their plan includes a designated number of requests. A request involves our cloud app verifying if an IP address is permitted to initiate a login attempt. This critical function forms the core of the premium cloud app, enabling us to identify malicious IPs preemptively, thwarting login attempts before they occur.
How Attacks Are Handled With The Free Version
When utilizing our free plugin, your site bears the burden of absorbing all attacks on its resources. Whether you're on shared hosting with GoDaddy, a managed hosting service, or a VPS, your hosting platform must deploy its own resources to handle the incoming requests from these attacks. This may result in your site experiencing sluggish performance or even going offline altogether.
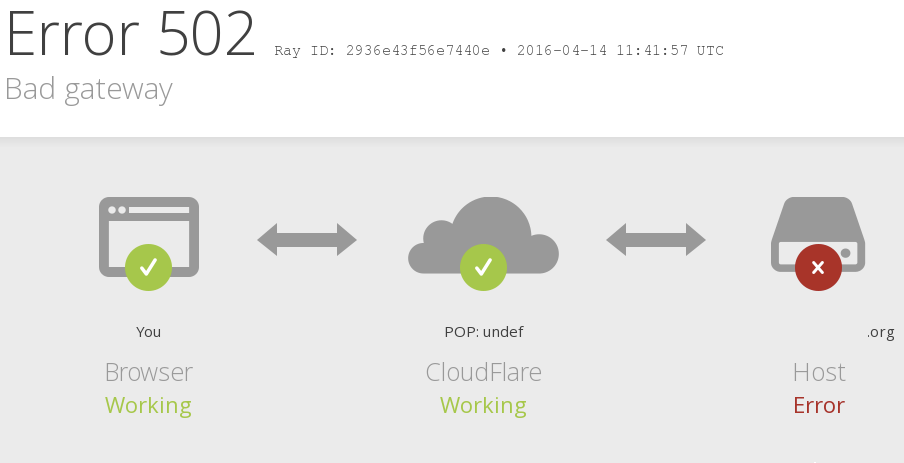
In fact, this is the predominant cause of your site's sluggishness, as your hosting provider lacks the infrastructure to repel brute-force attacks. While some providers do furnish DDoS protection, it's a distinct service that often incurs significant costs due to the substantial strain it places on their infrastructure.
How Requests Protect Your Website
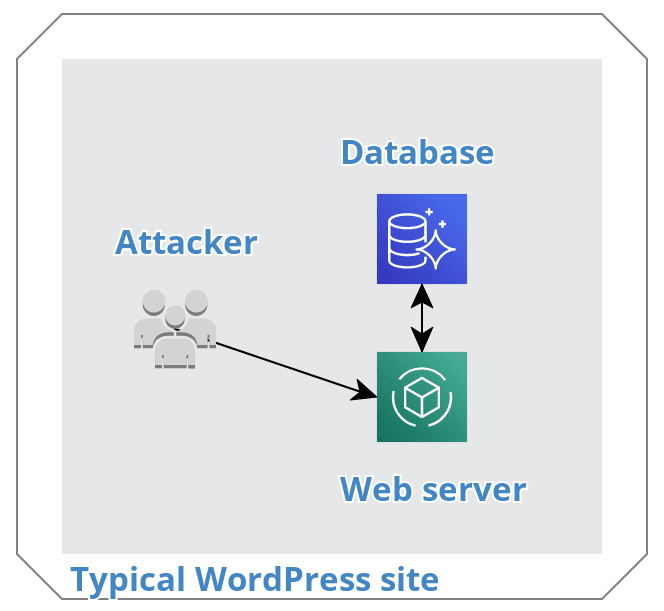
In this diagram above, there is nothing to protect your web and database servers from attacks. Our cloud app extends your infrastructure to work with Amazon's unlimited resources. It handles the dangerous IP lookups and copies some of your data (related to the plugin) into a server-less data structure on Amazon that's similar to a database.
In the diagram below, you can see how requests are made without disturbing your database, but you have a limited amount of them because they do consume CPU and memory resources of our Amazon infrastructure. Each login attempt can require up 1 to 2 requests. It depends if the IP is known or not.
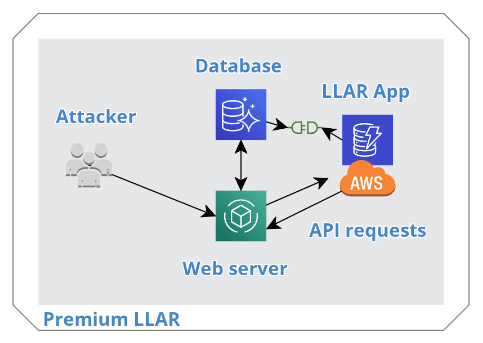
We've determined that 100K requests per month is sufficient for a site with traffic under 100 visitors per day. As the site becomes more popular 200K or 300K might be needed.
Definitions
We've created some simple definitions to help you understand how we categories different functions of the system.
Request: The process of our cloud app checking whether an IP address is allowed to create a login attempt.
Allowed Request: A request from an IP address that was allowed based on rules.
Denied Request: A request from an IP address that was denied based on rules.
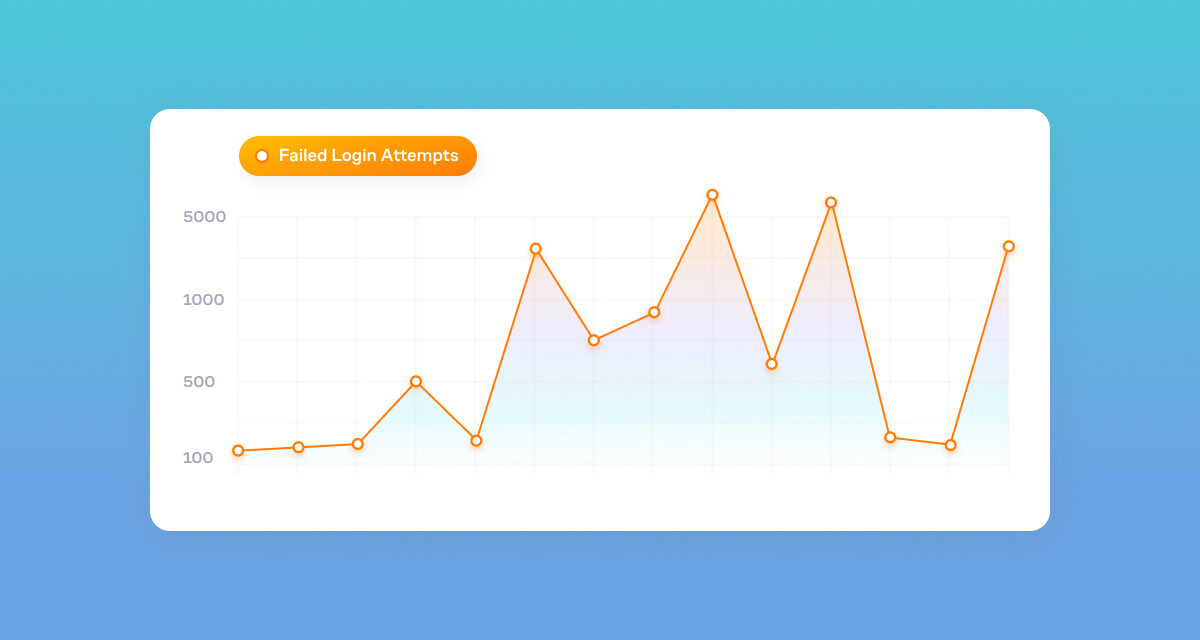
Login Attempt: An IP attempting to login to your website that is not already denied by the cloud app.
Failed Login Attempt: An IP that hasn't been previously denied by the cloud app, but has made an unsuccessful login attempt on your website.

Conclusion
In summary, requests play a crucial role in safeguarding your WordPress website against brute force attacks. Without these requests, your website lacks the capability to assess the malicious nature of IPs, potentially leading to increased failed login attempts and a higher risk of unauthorized access. We recommend exploring our premium plans to integrate this essential functionality into your website's security measures.
Frequently Asked Questions
You'll know if you have enough requests by reviewing your monthly usage. If you are running out of requests, we recommend upgrading to a different plan with more requests.
When using our free plugin, your website bears the brunt of absorbing all attacks, potentially leading to sluggish performance or even downtime.
Requests are made without disturbing your local database servers because the cloud app is handling the dangerous IP lookups using our cloud app.