When it comes to WordPress security, changing the admin login URL is often seen as a safeguard against unauthorized access. While the intention behind this practice may seem helpful, there are compelling reasons to reconsider. This is why the team at LLAR have decided to not include this feature in the core plugin features. In this article, we'll dive into the intricacies of altering your login URL, and why it's risky.
Security Through Obfuscation
WordPress users often consider changing the default admin login URL with the intention of bolstering their site's security. The default login URL, commonly known as /wp-admin, is seen as a potential vulnerability. By altering this URL, users believe they can obscure a crucial entry point for malicious actors attempting unauthorized access. This desire for enhanced security is rooted in the notion that security through obscurity—making key elements less visible—deters potential attackers. While the intention has merit, users must weigh the perceived benefits against the practical drawbacks. This includes the impact on SEO, plugin compatibility, and overall site maintenance.
Additionally, some WordPress users may have experienced or heard about brute force attacks targeting the default admin login page. These attacks involve automated scripts attempting to guess usernames and passwords repeatedly until they gain access. Changing the login URL is a strategy to stop brute force attacks by introducing an extra layer of complexity. This proactive stance towards security minimizes vulnerabilities and protects WordPress sites against evolving cyber threats.

Should you Hide the WordPress Admin Login URL?
Are you thinking on hiding your WordPress admin login URL? It's crucial to understand the risks involved. Here our 3 reasons every web administrator must consider before making this change.
Plugin compatibility issues
WordPress is renowned for its extensive library of plugins that enhance functionality. However, altering the admin URL may render some of these plugins incompatible or dysfunctional. Many plugins rely on the default URL structure to interact with the core of WordPress seamlessly. When this structure is modified, it can lead to conflicts, causing plugins to break. For example, plugins such as Limit Login Attempts Reloaded rely on the default URL structure to interact seamlessly with WordPress core.
Increased maintenance complexity
Changing the WordPress admin URL introduces an additional layer of complexity to your website's maintenance. While the intention might be to enhance security, the practical implications can be counterproductive. With a modified admin URL, every update or change related to WordPress core and its associated themes and plugins becomes a potential point of friction.
This increased complexity in managing updates not only demands more time and attention but also raises the likelihood of overlooking critical updates. As a result, the security posture of your site may be compromised rather than strengthened.
Limited security enhancement
Contrary to popular belief, changing the admin URL does not provide a foolproof security solution. Hackers and malicious bots are adaptive, and security through obscurity—relying on a non-default URL—offers only a limited defense. In fact, sophisticated attackers can easily discover the modified URL through various means, such as scanning tools or by exploiting vulnerabilities in other parts of your website.
The effort invested in changing the admin URL might provide a false sense of security without delivering substantive protection. Attacks to the WordPress admin login URL will not stop and will respond with 404 errors, which may require significant resources from your web server. The only way to completely block IPs is by setting up a reverse proxy, which requires the assistance of an IT professional.
Consequences of Changing the WordPress Admin Login URL [Examples]
Here are some potential consequences and real world examples of changing the admin login URL:
- Plugin/Theme Compatibility Issues
- Critical Updates Overlooked
- Increased Resource Consumption
Consequence 1: Plugin Compatibility Issues
Website A decided to change its WordPress admin login URL to enhance security. However, this decision led to conflicts with several plugins, including a popular e-commerce plugin. As a result, users experienced difficulties with online transactions, and the website's functionality was compromised. Website A ultimately had to revert to the default login URL and search for alternative security measures.
Consequence 2: Critical Updates Overlooked
Company B, a growing e-learning platform, changed its admin login URL to thwart brute force attacks. While the initial change seemed beneficial, it introduced complexity to their site maintenance process. With a modified admin URL, every update or change related to WordPress core and its associated themes and plugins became a potential point of friction. Company B's administrators found themselves spending more time on maintenance tasks and occasionally overlooking critical updates. Consequently, the security of their site was inadvertently compromised.
Consequence 3: Increased Resource Consumption
Blog C, a personal blog with limited resources, opted to change the admin login URL as a security measure. However, determined attackers managed to discover the modified URL through scanning tools, rendering the effort less effective. Blog C also faced issues with increased server resource consumption due to the 404 errors generated when attackers attempted to access the hidden login page. To achieve robust security, Blog C eventually decided to implement other security measures, such as 2FA and login attempt limiting.
Case Study: XYZ Corporation's Effective Security Approach
XYZ Corporation, a prominent e-commerce company, initially considered changing their admin login URL to combat brute force attacks. However, after assessing the potential consequences, they chose a different path. XYZ Corporation implemented strong password policies, enforced unique usernames, and installed the Limit Login Attempts Reloaded (LLAR) plugin to limit login attempts. This comprehensive security strategy not only thwarted brute force attacks but also ensured compatibility with their extensive range of plugins. By avoiding the complexities of URL modification, XYZ Corporation maintained a seamless user experience while significantly improving their website's security.
Best Alternatives to Changing WordPress Admin Login URL
You don't have to change the WordPress admin login URL to still receive significant protection from hacker. Try these tools and tips to get the job done without compromising the WordPress core files.
- Implement strong account policies
- Create Strong Passwords For Your Accounts
- Disable Default Usernames
- Change Permission on User Accounts to Limit Access
- Limit excessive login attempts
- Install Limit Login Attempts Reloaded (Free)
Implement strong account policies
- Create Strong Passwords For Your Accounts: Utilize 16 digit passwords to protect your accounts against unauthorized access, enhancing overall security. It would take a hacker 1 trillion years to break a 16 digit password with uppercase letters, lowercase letters, numbers, and symbols.
- Disable Default Usernames: Eliminate the risk associated with predictable default usernames by disabling and enforcing unique ones.
- Change Permission on User Accounts to Limit Access: Enhance security by customizing user account permissions, restricting access and mitigating potential vulnerabilities.
Limit excessive login attempts
Install Limit Login Attempts Reloaded (Free) to protect your site from excessive login attempts. LLAR will limit the amount of failed login attempts an IP can make, and deny future attempts with increased lockout windows. If you opt for Limit Login Attempts Reloaded Premium, you'll take advantage of the login firewall, which will detect and neutralize malicious IPs before they can attempt a login. LLAR doesn't change any core WordPress files so you can rest assure that any updates will not break your website.
Block IPs by country
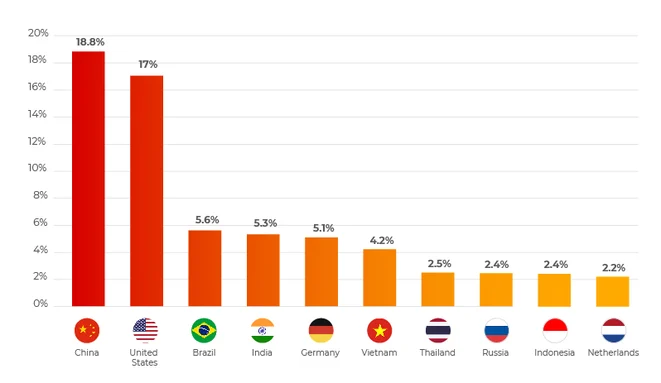
Significantly reduce the amount of activity on your login page by blocking IPs from other countries. By blocking login attempts from specific countries known for high rates of cybercrime or unauthorized access, you reduce the potential attack surface and make it more challenging for malicious actors to compromise your site.
The LLAR plugin allows admins to block (or allow) IPs by country with just a few clicks
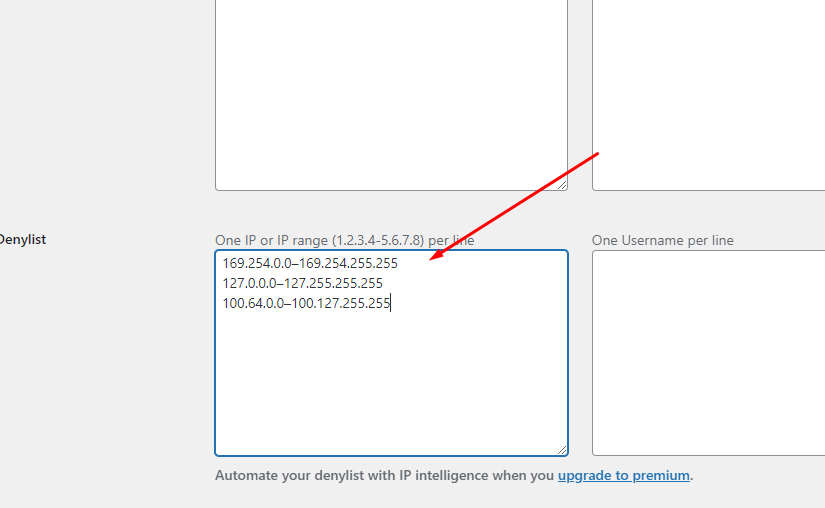
- Install and activate the free LLAR plugin.
- Go to the LLAR dashboard. Then go to the Logs tab, and scroll down to the Denylist field.
- Create an access control list with the IP ranges of the specific countries you want to block. You can use services, such as ip2location and countryipblocks to do this.
- Copy and paste the IP ranges into the Denylist field.
We strongly advise opting for the premium version of the LLAR plugin to enable country-based login blocking due to the labor-intensive nature of the manual approach. Implementing country blocking manually entails adding numerous lines of code, potentially numbering in the hundreds or even thousands, to block individual suspicious IP addresses and ranges. Moreover, IP ranges are dynamic and necessitate frequent updates. Please note that this method does not support IPV6 ranges.

Implement 2FA (Two-Factor Authentication)
Implementing two-factor authentication (2FA) on your WordPress site significantly enhances its security by adding an extra layer of defense beyond just a password. With 2FA enabled, even if malicious actors manage to obtain or crack a user's password, they would still need a second form of verification, typically a temporary code sent to a mobile device or generated by an app.
This additional step mitigates the risk of unauthorized access, and the overall integrity of your website. Given the prevalence of password-related breaches and the increasing sophistication of cyber threats, 2FA is a crucial security measure for safeguarding your WordPress site.
Conclusion
Hiding the admin login URL in WordPress might seem like a plausible security measure, but it can lead to unintended consequences and is generally not considered a best practice. Security through obscurity is not a reliable defense, and determined attackers can still discover the login page using various methods. Moreover, obscuring the login URL can complicate the user experience for legitimate administrators and contribute to confusion. A more effective approach to securing the login process involves implementing robust security measures such as strong unique passwords, 2FA, limiting logins with security plugins, and regular software updates.
Frequently Asked Questions
No. Even though you may receive some relief from brute force attacks, the consequences of changing the default file structure may impact overall performance and security.
Your website may receive limited security enhancement, but the overall integrity of your WordPress installation will be at risk due core file structure changes.
The best way to keep your website protect without changing the WordPress admin login URL is to have strong account policies, limit logins, deny countries by IP, and install a reputable security plugin.